When it comes to Cloud deployment, security is top of mind for all concerned. The Infor CloudSuite team uses best-practice protocols and a thorough, continuous improvement approach that gives you both confidence and peace of mind. The following information provides a detailed look at Infor’s security approach.
Defense-in-depth
Infor CloudSuite does not rely on any single security device, technique, or practice for data assurance. Instead, Infor CloudSuite employs a “defense-in-depth” strategy to implement multiple layers of overlapping security that safeguard your data through each link of the chain and ensure a high level of solution availability.
These security controls are enforced by a team of specialists who are constantly monitoring and improving our security posture to stay ahead of threats.
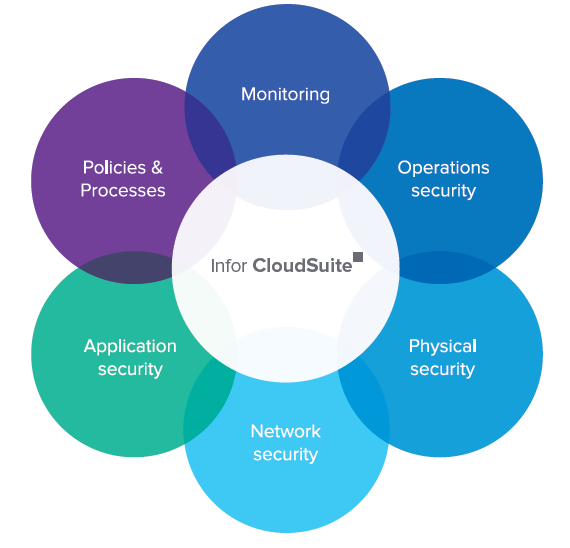
Infor CloudSuite security
1. Application security
To ensure security is built into Infor’s applications from the start, security requirements for each product are defined and then architected into the software design. Code reviews allow product teams to share secure coding practices they have gathered through own research or past implementations, while a focus on the Top 10 Open Web Application Security Project ensures that the most prevalent threats are being acknowledged and mitigated.
2. Network security
Security through separation
Infor CloudSuite’s networks are independent, meaning they are separated from the general Infor corporate network.
Layered defense architecture
Infor CloudSuite’s emphasis on security has resulted in an architecture that has multiple layers. These layers are built to protect against both very specific attacks (e.g., DDoS) and more general information gathering attacks (e.g., vulnerability scanning). The implemented mechanisms have the ability to proactively defend against an attack, while also providing real-time monitoring of current threats from the Internet.
Wired and purposeful—never wireless
At no point is traffic within the Infor CloudSuite network broadcast from an antenna or wireless transmitter that would expose it to interception by third parties equipped for wireless snooping, now a sophisticated and accessible field.
Secure environment in an insecure world
The Infor CloudSuite system had to be designed to maintain network security even when serving clients who don’t use best security practices. For example, Infor CloudSuite would need to be protected from a user with a compromised system not running the latest anti-virus protection.
Read more: Boost Productivity with Infor CloudSuite Industrial 9.01
3. Physical security
Physical security of Infor CloudSuite’s IT infrastructure
Physical security is paramount and pervasive throughout the implementation of Infor CloudSuite. However, it is most easily identified around our best-in-class data centers. These biometric-protected data centers house the solution’s network and IT infrastructure.
4. Operations security
IT infrastructure security
Infor CloudSuite’s strategic IT services are built, maintained, and administered in compliance with the security standards required for global data centers. In addition, technical elements of Infor CloudSuite security are supported by operational practices.
Infor CloudSuite’s security ethic has been carried over into the structure of its operations, where specific teams have prescribed roles and responsibilities. Access to critical Infor CloudSuite systems is structured to ensure separation of duties and administered under the principle of least privilege.
Strict data transmission protocols
The architecture of the Infor CloudSuite software allows Infor to leverage the concept
of defense-in depth-security by using technologies such as SSL/TLS and transaction-based business logic.
Encryption and privacy
Encryption is used extensively within the Infor CloudSuite environment to ensure that data is protected. While in-transit, data is encrypted using appropriate mechanisms that include TLS/SSL, PGP, and secure FTP. When required, data-at-rest is encrypted using database, file system, or other appropriate encryption capabilities.
Read more: Manufacturing ERP Review: Infor CloudSuite Solutions
5. Monitoring
Dynamic password management
Infor CloudSuite maintains centrally managed passwords to protect administrative access points to the
Infor CloudSuite network, applications, and IT infrastructure. To defeat password cracking by brute force, the system registers unsuccessful password attempts and patterns, alerting network management staff to investigate.
Management of digital certificates
Every secure session with a web server has an important aspect—the ability to authenticate the server. Certificates are the foundation of a secure cloud implementation, where each primary element of the Infor CloudSuite solution presents a verifiable identity.
Managed configurations
When Infor CloudSuite’s network and systems architects design and configure our systems, they make choices that promote and enable security.
Data ownership
Within Infor, customers own their data, and it is accessible at all times. Customers can also have all data returned at the end of the engagement.
Logging, monitoring, auditing, and incident response
Infor CloudSuite’s staff monitors the network using a set of tools, specifically configured for this solution, to effectively manage logs and alerts.
Customer data not captured by monitoring processes
The only network details collected by our logging and auditing systems are application, system, and network logs and metadata. Our policy is to not collect log information that contains actual customer data.
Security event recognition
Infor CloudSuite security encompasses monitoring, characterizing, reporting, and handling of security incidents, including technical escalation and customer notification paths.
Policies and procedures
Infor CloudSuite has implemented a comprehensive security policy that focuses on the ISO 27001 best practice standard to provide the guiding principles for our focus on confidentiality, integrity, and availability.
ISO-27001 compliance
The ISO-27001 standard is an internationally recognized credential of a securely designed and soundly run information security management system.
SSAE 16 assessments
The Infor CloudSuite’s Data Centers undergo SSAE 16 SOC 1 Type II assessments to provide an independent auditor’s assessment of the controls and adequacy of the identified controls in meeting their objectives.
Regulatory compliance
Whenever an application deals with data that requires regulatory compliance (e.g., HIPAA, SOX, PCI, GLBA, regional privacy laws, etc.), Infor CloudSuite works with customers to ensure that the controls needed to meet those requirements are in place.
 English
English  Vietnamese
Vietnamese 

