Financial data must be protected from unauthorised access to safeguard the privacy and cyber security of an individual or organisation. Therefore, this is one of the biggest concerns of companies wanting to protect their financial information. For businesses that are using SunSystems, TRG has already provided optimal solutions in order to keep financial data safe from theft or data leakage.
So what are those solutions that TRG has deployed?
Read more: Move Your Accounting to the True Cloud with SunSystems Cloud

Firstly, TRG applies AWS (Amazon Web Services) Cloud Security as the highest priority. AWS is a secure cloud services platform, database storage, content delivery and other functionality to help businesses scale and grow. Basically, AWS uses many layered controls, continuous validation and testing to ensure that the fundamental infrastructure is monitored and protected 24/7.
Read more: How AWS Manages and Maintains Their Massive Data Centres
Besides, AWS also makes sure that these controls are updated for every new data centre and service. Additionally, AWS operates under a shared security responsibility model, where AWS is responsible for the security of the based cloud infrastructure and users are responsible for securing workloads deploying in AWS (see Figure 1).
This model gives users the flexibility they need to implement the most applicable security controls for business functions, especially SunSystems Cloud. Consequently, it allows users to create private networks and prevent unexpected network access.
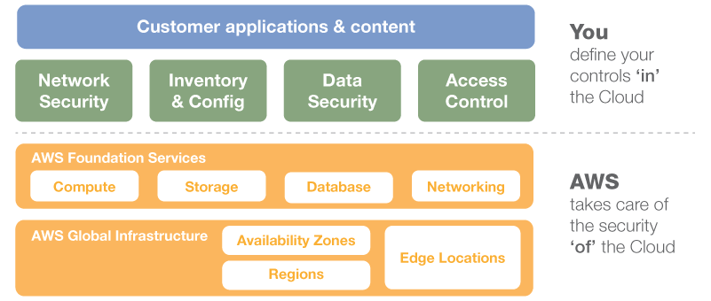
Figure 1: AWS Shared Security Responsibility Model
Another security layer that SunSystems Cloud uses is Qualys Vulnerability Management (VM). Qualys VM is a cloud-based service that provides protection to IT systems which might be vulnerable to the latest Internet threats and unpredicted changes in the network.
For example, Qualys VM has the ability to create an interactive network map that shows the perimeter and internal devices. As a result, an administrator can generate a map that displays domains, hosts, connected endpoints, routers and other networking devices.
Furthermore, clicking a host in the map indicates details about that host, such as operating systems, date of last scan and ports in use. Consequently, the administrator of SunSystems Cloud will rely on the continually updated database of vulnerability signatures in order to minimise the security risks.
In conclusion, all information of SunSystems Cloud is protected by two excellent security programs which are Amazon Web Services and Qualys Vulnerability Management. Besides, SunSystems Cloud is always improved and developed in order to provide the best solutions to businesses.
Please subscribe to our Blog so you won’t miss future articles or request a free demo to see an automated solution by clicking on the button below:
 English
English  Vietnamese
Vietnamese 


