The hospitality industry handles loads of sensitive data on a daily basis, from the customers’ reservation information to their flight details and payment records. Having all these private data on hands makes hotels the prime targets for cyber-attacks. In the case of internationally recognised brands that house F&B and retail outlets within the hotels, it’s even more challenging to resolve the data issues. To effectively safeguarding hotel data comprising of not only your customers but also your employees’ personal data, hoteliers need to first identify the elements that roadblock your ways to success.
Read more: Rise of Chief Data Officer (CDO) to Solve the Data Issues

Big Data in the hospitality sector
In order to manage personalised experience, the hospitality industry needs advanced data analytics solution. Customers leave a huge amount of data behind after every check-in and check-out. It is not only personal and contact information but also about the kinds of services they used, the kinds of foods they ordered, the facilities such as meeting rooms, tennis courts and swimming pool they booked.
These data sets are multiplied by tens or hundreds of entities owned by the corporation. The era of paper records is long gone. Everything now has to run digitally and be put into databases.
It all starts with the traditional three-party relationship
Hotels, particularly the branded ones, are susceptible to cyber theft due to the complicated three-party relationship that surrounds the franchisor, the hotel’s owner, and the hotel’s operator.
- The franchisor (or the brand): owns the brand, can impose which reservation system the hotels within the group must use. The franchisor also owns all the data collected and inputted into the system.
- The owner: a group of investors or individuals who have a varying degree of involvements in handling operational issues. The owner can install a separate point-of-sale (POS) systems for non-room services.
- The operator: collects, inputs, stores, and maintains both guests and employees’ data. The operator is also responsible for providing security training to the employees.
The ownership of the data obtained and the disparate management systems have caused tension among these three main players. As mentioned above, the franchisor mandates the reservation and management systems but the owner can install their own card payment solutions for their non-room services.
Read more: Providing Stellar Service for Hotel Guests with Social Collaboration Tool
Challenges in safeguarding hotel data
Challenge #1: Payment via POS system
Payment by card has become increasingly popular due to its convenience. Hotel guests during their stay would make payments via their corporate cards or personal cards at least once. This essentially turns hotels into treasure troves for hackers to mine at any time.
There have been reports stating the majority of attacks occurred at hotels were from the POS systems. POS remains to be an attractive target despite emerging technologies, like Europay-Mastercard-Visa (EMV) card readers and point-to-point encryption (P2PE), are present to strengthen the security network against malware.
Credit card data is mainly stored in a plain text form in the POS machine memory which is prone to attack through the memory-scraping capabilities. This blog post by Alien Vault explains pretty clearly the different variants of malware with an infographic detailing multiple big brands that experienced this issue.
As noted above, the hotel owners would install their preferred POS systems for the F&B or retail outlets within the hotel precinct. The franchisors, though take ownership of all data input into the reservations and management systems (or otherwise specified in the agreement), data stored in the POS machine is not their responsibility. As such, it comes down to the owner and the POS service provider to ensure all security measurements are carried out and acted upon in a way that the guests are best protected.
Read more: Internet of Things from the F&B Industry Perspective
This also puts tension on the relationship between the owners and the operators as the operators are in charge of the implementation of the POS systems as well as the day-to-day handling of data. The operator also is obligated to act in accordance with the Payment Card Industry Data Security Standard (PCI-DSS).
Having said that, not many hotels have the resources needed to upgrade their systems to the latest version. Many still accept payment via phone or fax which is not at all ideal.
Challenge #2: Human error
Phishing scams and human error are among the top causes of data breaches. Just like how technologies evolve over time, so do the tactics or procedures of the attackers. Phishing scams are low cost but are highly effective as they exploit the weaknesses in the human nature. Many attackers rely heavily on this technique to bypass the hotel’s security networks.
Examples of human error that affecting hotel’s security including:
- employees leave their laptops (which contains sensitive data) unmonitored
- employees are given access to information beyond their responsibilities
- staff emails sensitive data to unintended personnel
- employee’s access is not revoked immediately after they quit
In the industry with high employee turnover like hospitality, the ability to keep track of the current active workforce, equip them with appropriate cyber threat training is a real challenge for any operator. Also noted that not only the guests’ data is at risk, without the necessary protection, your employees’ personal data (social security numbers, tax file numbers, bank accounts, etc.) is also subjected to cyber theft.
Failing to acknowledge the human element in data protection can postpone organisations to come up with solutions to at least minimise such threat.
Read more: What ‘Transformers’ Can Teach Us about Enterprise IT Security
What hotels can do to strengthen their defence mechanism?
There is no guarantee that cyber threat will be completely wiped out one day. Hoteliers must always stay on their feet, be extra cautious in safeguarding sensible information both digitally and physically.
1. Clearly define liabilities, data handling requirements
Franchisors, owners, and operators when dealing with each other as well as with third parties (such as software providers, suppliers, contractors, etc.) need to be in it together to combat cyber threats. If the issues occur to one, they can escalate and can quickly get out of hand.
Be specific in terms of what each party requires from the other. For example, a request for cyber incident indemnification can help protect the hotels’ financial situation when disaster strikes. Furthermore, enforce PCI-DSS (or other equivalent policies) to be carried out at all outlets to help keep risks at bay.
2. Protect data with advanced technologies
Considering the majority of cyber-attacks at hotel stemmed from POS systems, hotels must be extra careful when selecting a vendor. Incorporating new technologies in encrypting POS data and act in accordance with PCI-DSS can (a) help to maximise security, and (b) protect hotels against legal issues.
Examples of technologies available that can boost security: end-to-end encryption (or point-to-point encryption), “smart chips” card readers, “tokenization”.
Cases of lost or stolen devices and equipment that stored sensitive data will continue to happen. In addition to training the employees to follow strict policies when managing and maintaining these devices and equipment, hotels should also implement full encryption to avoid the worst case scenario. Many regulators consider the full encryption to be the standard requirement; lack thereof is deemed to be insufficient.
3. Employee training and awareness
Set up simulated training sessions where all types of scams, malware, cyber and physical theft are tackled to raise awareness and help equip your employees with the necessary knowledge to manage the situation when the crime actually happens.
Read more: How to protect your data when employees leave
Employee training should be included as part of every induction process and frequently revised to ensure the programs are up-to-date. These programs act as a baseline for organisations to measure the current security systems as well as the users that are most susceptible to threats. Having a well-documented anti-phishing program will put hotels in better position combatting breaches in security.
In addition, hotels should also frequently assess the access granted to employees. Those who do not need to access certain levels of information should have their passes restricted or terminated.
4. Passwords are not enough for data security
Passwords are the cornerstone of cyber security. The problem is that users tend not to follow the recommended best practices to make their passwords secure. Additionally, passwords can be leaked due to security breaches.
For instance, 68 million Dropbox user credentials were stolen in an incident in 2012. Since such risks are escalating, organisations have been working hard to find better alternatives whose effectiveness varies. Even though passwords may not completely be replaced anytime soon, these alternatives will, without a doubt, provide much-needed additional data security layers.
Security questions are probably the most common policy used in tandem with passwords. They are usually about the users’ background and habits. The main problem with security questions is that they are researchable. So it is not particularly hard for attackers to figure out the answers to these questions.
Two-factor authentication is getting more and more popular, especially among financial organisations. Apart from passwords, users also need a randomly-generated code that is sent to their security tokens or cell phones. Two-factor authentication is now a feature in most online banking systems. Still, there is a risk of stolen tokens or phones.
Many organisations are betting on biometric security, in which a user’s identity is verified by biometrics such as fingerprints, voice or facial patterns. Such features are unique to each individual. Biometric authentication systems are getting increasingly sophisticated and affordable to be widely deployed. HSBC, for example, is rolling out biometric security apps, for iOS and Android devices, replacing passwords or PIN numbers.
Biometric security systems are not unbreakable, however. Fake gelatine fingerprints were shown to be able to fool fingerprint scanners. Facial recognition technology also can be fooled by photographs.
Some experts, therefore, suggest that biometrics should be used as an alternative to usernames rather than to passwords. For example, users will scan their fingerprints then key in passwords. Biometrics can also be used in the two-factor authentication process.
5. Mitigate the risk of disgruntled employees
Employees come and go; it is a stark reality of the corporate world. Unfortunately, half of employees who leave their jobs also take confidential corporate data with them according to research conducted by Symantec in 2013. And 40% of them intend to use such data in their new jobs. You need to take proactive measures to protect your data when your employees move on, because the consequences could be severe for your business if you don’t.
Many employers may assume the risk of losing sensitive data mostly comes from outside attacks and therefore do not have a well-established data security policy regarding their own employees. In fact, the 2014 US State of Cybercrime Survey indicated that insiders caused 37% of reported cybercrimes. And this threat does not only come from disgruntled employees with malicious intentions. Some employees think it is acceptable to keep and use the data they created.
Compounding this problem is the proliferation of BYOD (Bring-Your-Own-Device), which makes it easier for departing employees to leave with the data in their devices, and not to mention such devices when connect to the enterprise network may compromise the security measures. To what extent can the company access and control the employees’ devices to enforce data protection policies?
Here is a guide to safeguard your critical data from leaving with your departing employees.
Legal and ethical implications of collecting personal data
Collecting personal data from your guests also creates some legal and ethical challenges. Around 40% of travellers are willing to share their data in exchange for tailored and relevant offers, according to research by Amadeus. On the other hand, nearly 90% of customers want to control how companies use their collected data.
Privacy and data protection is the centrepiece of many recent prominent debates and legislative actions around the world. Consequently, be sure to provide your guests with a clear policy of what data you are collecting, what you are using it for, as well as an opt-out option for those who do not wish to provide their personal data.
You need to establish and enforce robust data security measurements to protect your guests’ data as if it were your own. Guard against security breaches from people not only outside but also inside your organisation. The last thing you need is your own “Snowden” incident. Choose trusted vendors to protect your data and review the security plans regularly.
In the realm of mass personalisation, there is a fine line between being helpful and being intrusive. Guests would probably not appreciate the fact that you count how many martinis they had last night or comb through their medicine cabinet or dresser drawers.
And it is not only the matter of what type of data you are collecting, but also how you provide your messages or offers. For instance, a study from Accenture concludes that most customers find interrupting their buying activity with recommendations undesirable.
In order to avoid crossing such lines, you should ensure that the data being collected is really to help enhance your guests’ experience first and foremost, rather than just improve your own bottom line. A study from Yahoo suggests that three-fourths of customers have no objection when you collect data about:
- What content they have viewed and for how long
- Keywords they have used for searching
- Ads they have clicked
- Products or offers they have browsed
The very nature of the hospitality industry makes personalisation an imperative. Everyone loves to be treated as an individual. Personalisation has been demonstrated to drive increased customer satisfaction and bottom lines. Hoteliers should remain mindful that this strategy is not just about technology, but a complete transformation of how hotels operate.
How to prevent ransomware with these 4 practices
1. Secure buy-in from management and end users
Senior management needs to back any ransomware prevention measure before it gets off the ground. Similarly, the IT department also needs to get the end users onboard by clearly explaining to them the impacts of those security measures and the expected behaviours from the end users.
2. Choose suitable technologies
Patching needs to be well-managed, especially regarding third-party patches. Move toward more advanced malware protection tools. Frequent data backups are essential. Network segmentation should also be deployed properly.
3. Monitor and respond
The cyber security team needs to monitor servers, workstations, and networks, and to take prompt actions to respond to any detected threat.
4. It is not a one-off deal
Ransomware prevention is not a one-time project that will take care of itself. The IT function needs to have a long-term and holistic approach to the problem.
How data security is implemented in the cloud
When it comes to Cloud deployment, security is top of mind for all concerned. The Infor CloudSuite team uses best-practice protocols and a thorough, continuous improvement approach that gives you both confidence and peace of mind. The following information provides a detailed look at Infor’s security approach.
Defense-in-depth
Infor CloudSuite does not rely on any single security device, technique, or practice for data assurance. Instead, Infor CloudSuite employs a “defense-in-depth” strategy to implement multiple layers of overlapping security that safeguard your data through each link of the chain and ensure a high level of solution availability.
These security controls are enforced by a team of specialists who are constantly monitoring and improving our security posture to stay ahead of threats. Continue reading >>
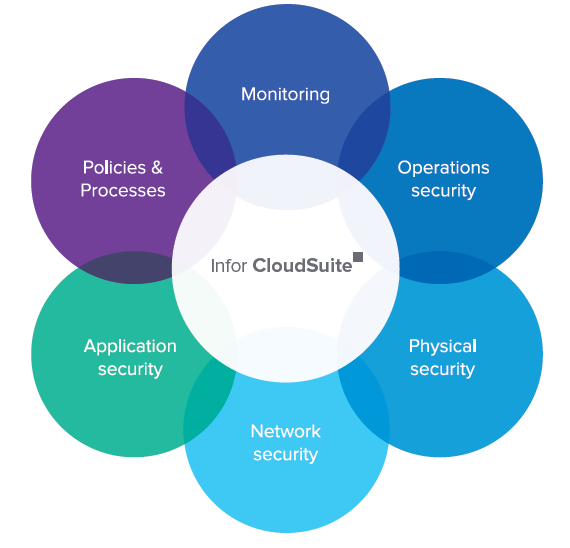
Infor CloudSuite security
1. Application security
To ensure security is built into Infor’s applications from the start, security requirements for each product are defined and then architected into the software design. Code reviews allow product teams to share secure coding practices they have gathered through own research or past implementations, while a focus on the Top 10 Open Web Application Security Project ensures that the most prevalent threats are being acknowledged and mitigated.
2. Network security
Security through separation
Infor CloudSuite’s networks are independent, meaning they are separated from the general Infor corporate network.
Layered defense architecture
Infor CloudSuite’s emphasis on security has resulted in an architecture that has multiple layers. These layers are built to protect against both very specific attacks (e.g., DDoS) and more general information gathering attacks (e.g., vulnerability scanning). The implemented mechanisms have the ability to proactively defend against an attack, while also providing real-time monitoring of current threats from the Internet.
Wired and purposeful—never wireless
At no point is traffic within the Infor CloudSuite network broadcast from an antenna or wireless transmitter that would expose it to interception by third parties equipped for wireless snooping, now a sophisticated and accessible field.
Secure environment in an insecure world
The Infor CloudSuite system had to be designed to maintain network security even when serving clients who don’t use best security practices. For example, Infor CloudSuite would need to be protected from a user with a compromised system not running the latest anti-virus protection.
Read more: Boost Productivity with Infor CloudSuite Industrial 9.01
3. Physical security
Physical security of Infor CloudSuite’s IT infrastructure
Physical security is paramount and pervasive throughout the implementation of Infor CloudSuite. However, it is most easily identified around our best-in-class data centers. These biometric-protected data centers house the solution’s network and IT infrastructure.
4. Operations security
IT infrastructure security
Infor CloudSuite’s strategic IT services are built, maintained, and administered in compliance with the security standards required for global data centers. In addition, technical elements of Infor CloudSuite security are supported by operational practices.
Infor CloudSuite’s security ethic has been carried over into the structure of its operations, where specific teams have prescribed roles and responsibilities. Access to critical Infor CloudSuite systems is structured to ensure separation of duties and administered under the principle of least privilege.
Strict data transmission protocols
The architecture of the Infor CloudSuite software allows Infor to leverage the concept
of defense-in depth-security by using technologies such as SSL/TLS and transaction-based business logic.
Encryption and privacy
Encryption is used extensively within the Infor CloudSuite environment to ensure that data is protected. While in-transit, data is encrypted using appropriate mechanisms that include TLS/SSL, PGP, and secure FTP. When required, data-at-rest is encrypted using database, file system, or other appropriate encryption capabilities.
Read more: Manufacturing ERP Review: Infor CloudSuite Solutions
5. Monitoring
Dynamic password management
Infor CloudSuite maintains centrally managed passwords to protect administrative access points to the
Infor CloudSuite network, applications, and IT infrastructure. To defeat password cracking by brute force, the system registers unsuccessful password attempts and patterns, alerting network management staff to investigate.
Management of digital certificates
Every secure session with a web server has an important aspect—the ability to authenticate the server. Certificates are the foundation of a secure cloud implementation, where each primary element of the Infor CloudSuite solution presents a verifiable identity.
Managed configurations
When Infor CloudSuite’s network and systems architects design and configure our systems, they make choices that promote and enable security.
Data ownership
Within Infor, customers own their data, and it is accessible at all times. Customers can also have all data returned at the end of the engagement.
Logging, monitoring, auditing, and incident response
Infor CloudSuite’s staff monitors the network using a set of tools, specifically configured for this solution, to effectively manage logs and alerts.
Customer data not captured by monitoring processes
The only network details collected by our logging and auditing systems are application, system, and network logs and metadata. Our policy is to not collect log information that contains actual customer data.
Security event recognition
Infor CloudSuite security encompasses monitoring, characterizing, reporting, and handling of security incidents, including technical escalation and customer notification paths.
Policies and procedures
Infor CloudSuite has implemented a comprehensive security policy that focuses on the ISO 27001 best practice standard to provide the guiding principles for our focus on confidentiality, integrity, and availability.
ISO-27001 compliance
The ISO-27001 standard is an internationally recognized credential of a securely designed and soundly run information security management system.
SSAE 16 assessments
The Infor CloudSuite’s Data Centers undergo SSAE 16 SOC 1 Type II assessments to provide an independent auditor’s assessment of the controls and adequacy of the identified controls in meeting their objectives.
Regulatory compliance
Whenever an application deals with data that requires regulatory compliance (e.g., HIPAA, SOX, PCI, GLBA, regional privacy laws, etc.), Infor CloudSuite works with customers to ensure that the controls needed to meet those requirements are in place.
Safeguard your data the right way with the right Hospitality Management Solution. Request a demo now!
 English
English  Vietnamese
Vietnamese 


